How to configure VPN
How to configure VPN before going for practical, Let us understand why we need VPN (Virtual Private Network)
Privacy and Security: One of the primary reasons for using a VPN is to enhance online privacy and security. When you connect to the internet through a VPN, your internet traffic is encrypted and routed through a secure server. This encryption prevents hackers, government agencies, or malicious entities from intercepting and monitoring your online activities, such as the websites you visit and the data you transmit.
Now we understand the reason why we need a VPN, let us Understand How to configure VPN on a Router
INTRODUCTION TO HOW TO CONFIGURE VPN
The GRE (Generic Routing Encapsulation) protocol is a network protocol used in computer networking to encapsulate a wide variety of network layer protocols into point-to-point connections. GRE is often used to create private and secure communication tunnels over a public network, such as the Internet. It does this by encapsulating the payload of one network protocol within packets of another network protocol.

Here are some key points about the GRE protocol:
Tunneling: GRE is primarily used for creating tunnels between two endpoints, typically routers or firewall devices. These tunnels can carry a variety of network traffic, including IPv4, IPv6, and multicast traffic, among others.
Encapsulation: When data is sent over a GRE tunnel, the original packet is encapsulated within a new GRE packet. This encapsulation allows the data to traverse networks that might not support the original network protocol.
Flexibility: GRE is protocol-independent, meaning it can encapsulate different types of network traffic, making it versatile for various applications.
Routing: GRE tunnels can be used to connect remote networks securely, effectively extending a private network over a public infrastructure like the Internet. It can be used for site-to-site VPNs (Virtual Private Networks) and other forms of secure communication.
Minimal Security: While GRE itself does not provide encryption or security features, it can be used in conjunction with other security protocols and mechanisms to create secure communication channels.
Header Overhead: GRE adds its own header to the encapsulated packets, which increases the overall packet size. This additional overhead should be considered in network design and capacity planning.

In summary, GRE is a protocol used for encapsulating various types of network traffic, allowing it to traverse networks that might not natively support the encapsulated protocol. It is commonly used for creating secure communication tunnels and extending private networks across public networks like the Internet.
Watch Practical in this Video
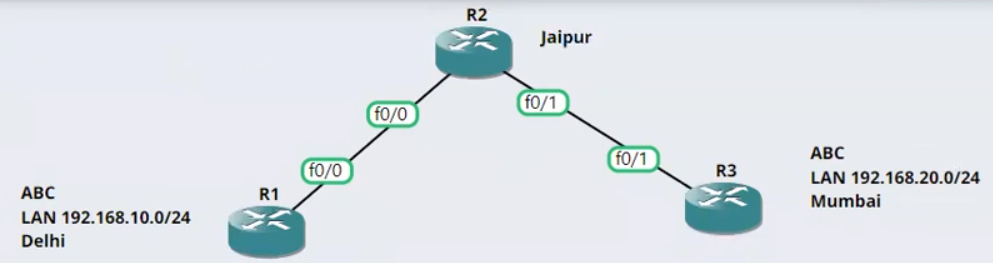
Configuration on Router (R1) STEP-1
Conf t
int f0/0
ip address 1.1.1.1 255.0.0.0
no shutdown
exit
int loopback 0
ip address 192.168.10.1 255.255.255.0
exitConfiguration on Router (R2) STEP-2
Conf t
int f0/0
ip address 1.1.1.2 255.0.0.0
no shutdown
int f0/1
ip address 2.2.2.1 255.0.0.0
no shutdown
exitConfiguration on Router (R3) STEP-3
Conf t
int f0/1
ip address 2.2.2.2 255.0.0.0
no shutdown
exit
int loopback 0
ip address 192.168.20.1 255.255.255.0
exit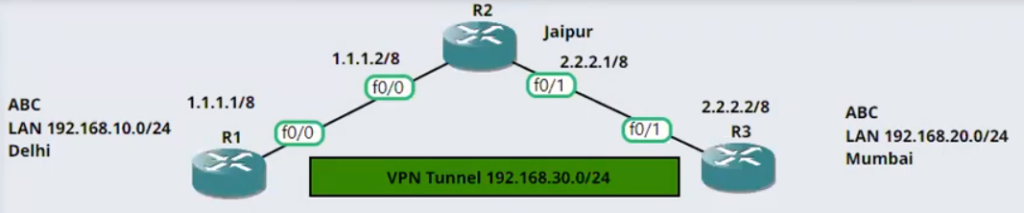
Configuration on Router (R1) STEP-4
ip route 0.0.0.0 0.0.0.0 1.1.1.2
int tunnel 0
ip address 192.168.30.1 255.255.255.0
no shutdown
tunnel source f0/0
tunnel destination 2.2.2.2
tunnel mode gre ipConfiguration on Router (R3) STEP-5
ip route 0.0.0.0 0.0.0.0 2.2.2.1
int tunnel 0
ip address 192.168.30.2 255.255.255.0
no shutdown
tunnel source f0/1
tunnel destination 1.1.1.1
tunnel mode gre ipConfiguration on Router (R1) STEP-6
ip routing
router ospf 100
router-id 11.11.11.11
network 192.168.30.0 0.0.0.255 area 0
network 192.168.10.0 0.0.0.255 area 0Configuration on Router (R3) STEP-7
ip routing
router ospf 100
router-id 22.22.22.22
network 192.168.30.0 0.0.0.255 area 0
network 192.168.20.0 0.0.0.255 area 0Great We have successfully Configured the VPN on the Router using GRE Protocol.
Learn Complete CCNA 200-301 or want to understand more Click here.
Hope this Article and practical will help you understand the technologies better in your practical network infrastructure.






[…] You may also be interested in How to configure VPN on Router […]