How to Build a Point-to-Point Tunnel
Introduction
Point-to-point tunnels are essential in various networking and communication scenarios. Whether you’re connecting remote offices, establishing a secure communication link, or simply optimizing your network infrastructure, knowing how to build a point-to-point tunnel is a valuable skill. In this guide, we will walk you through the steps and best practices to create a robust and reliable point-to-point tunnel. By the end of this tutorial, you’ll have the knowledge and confidence to set up these tunnels effectively, improving your network connectivity and security. Let’s get started on this journey of building efficient point-to-point tunnels.
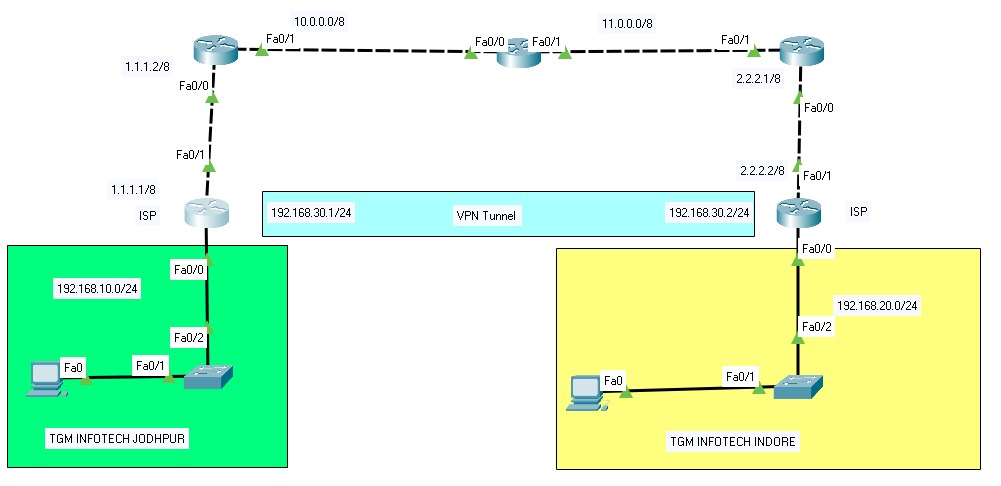
R1
Jodhpur Router
Building configuration...
Current configuration : 998 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname Jodhpur
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2811/K9 sn FTX10175PA7-
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface Tunnel0
ip address 192.168.30.1 255.255.255.0
mtu 1476
tunnel source FastEthernet0/1
tunnel destination 2.2.2.2
!
!
interface FastEthernet0/0
ip address 192.168.10.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 1.1.1.1 255.0.0.0
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 100
router-id 11.11.11.11
log-adjacency-changes
network 1.0.0.0 0.255.255.255 area 0
!
router ospf 200
router-id 66.66.66.66
log-adjacency-changes
network 192.168.10.0 0.0.0.255 area 0
network 192.168.30.0 0.0.0.255 area 0
!
ip classless
!
ip flow-export version 9
!
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
endR2
Building configuration...
Current configuration : 752 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R2
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2811/K9 sn FTX101777VQ-
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
ip address 1.1.1.2 255.0.0.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 10.0.0.1 255.0.0.0
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 100
router-id 22.22.22.22
log-adjacency-changes
network 1.0.0.0 0.255.255.255 area 0
network 10.0.0.0 0.255.255.255 area 0
!
ip classless
!
ip flow-export version 9
!
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
R3
Building configuration...
Current configuration : 754 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R3
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2811/K9 sn FTX1017O2P8-
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
ip address 10.0.0.2 255.0.0.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 11.0.0.1 255.0.0.0
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 100
router-id 33.33.33.33
log-adjacency-changes
network 10.0.0.0 0.255.255.255 area 0
network 11.0.0.0 0.255.255.255 area 0
!
ip classless
!
ip flow-export version 9
!
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
R4
Building configuration...
Current configuration : 752 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R4
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2811/K9 sn FTX1017F9I7-
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface FastEthernet0/0
ip address 2.2.2.1 255.0.0.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 11.0.0.2 255.0.0.0
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 100
router-id 44.44.44.44
log-adjacency-changes
network 11.0.0.0 0.255.255.255 area 0
network 2.0.0.0 0.255.255.255 area 0
!
ip classless
!
ip flow-export version 9
!
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
R5
Building configuration...
Current configuration : 997 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname INDORE
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2811/K9 sn FTX10171DBP-
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
!
interface Tunnel0
ip address 192.168.30.2 255.255.255.0
mtu 1476
tunnel source FastEthernet0/1
tunnel destination 1.1.1.1
!
!
interface FastEthernet0/0
ip address 192.168.20.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 2.2.2.2 255.0.0.0
duplex auto
speed auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 100
router-id 55.55.55.55
log-adjacency-changes
network 2.0.0.0 0.255.255.255 area 0
!
router ospf 200
router-id 77.77.77.77
log-adjacency-changes
network 192.168.30.0 0.0.0.255 area 0
network 192.168.20.0 0.0.0.255 area 0
!
ip classless
!
ip flow-export version 9
!
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end




