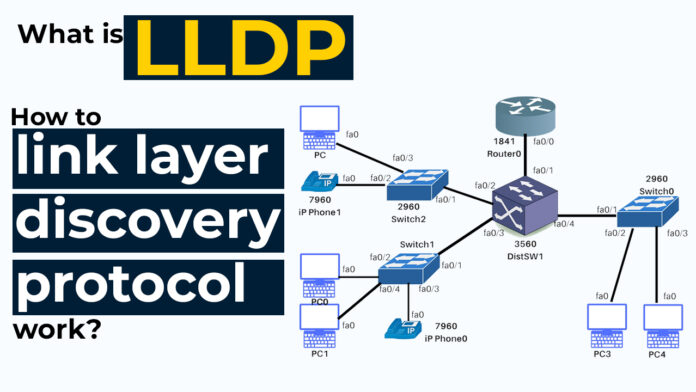
How to link layer discovery protocol work?
Introduction
The link layer discovery protocol (LLDP) is a fundamental networking protocol used to facilitate the automatic discovery and advertisement of information about devices within a local area network (LAN). This protocol is vendor-agnostic, ensuring compatibility across various networking equipment, and plays a pivotal role in modern network administration.
Here’s how LLDP operates:
- LLDPDU: An LLDP frame carries an LLDP Data Unit (LLDPDU), which is a structured packet containing various pieces of information about the sender device. This information is encoded in TLVs (Type, Length, Value) format.
- LLDP Frame: link layer discovery protocol operates at the data link layer (Layer 2) of the OSI model. When a network device is powered on or connected to a network segment, it periodically sends LLDP frames onto the network
- Neighboring Devices: Other neighboring devices on the same network segment receive these LLDP frames. Neighboring devices can include switches, routers, access points, and more.
- Database Formation: Each receiving device maintains an LLDP database that stores information about its neighbors. This database is continually updated as LLDP frames are received and processed.
- Network Management: LLDP data is valuable for network management tasks. It helps administrators monitor the status of network links, identify devices connected to specific ports, and troubleshoot network issues by providing detailed information about networked devices.
- Vendor-Agnostic: link layer discovery protocol is vendor-agnostic, meaning it’s not tied to any specific manufacturer or brand of networking equipment. This ensures interoperability and compatibility across a wide range of devices.
- Configuration Options: Network administrators can typically configure LLDP settings on their devices, specifying which information to advertise and how often to send LLDP frames.
- Topology Discovery: By analyzing the LLDP information from neighboring devices, a network administrator can build a map of the network’s physical topology. This map shows how devices are interconnected through switches and routers.
- Information Exchange: Upon receiving an LLDP frame, the recipient device extracts the LLDPDU and reads the TLVs to gather information about the sender. Common information shared through LLDP includes:
- CCNA 200-301 Self-Study: CCNA Certification is globally recognized and it is respected by most companies across the globe.

Fortinet Firewall : Fortinet Firewall-NSE4 validates your skills and knowledge of the Fortinet Firewall network security operating platform.

How to Become a Computer Network Expert: A Comprehensive Guide
- System Description: A brief description of the device.
- System Name: The name of the sending device.
- Capabilities: Information about the device’s capabilities, such as supported speeds and duplex modes.
- Management Addresses: IP addresses or other management addresses associated with the device.
- Port Identifier: The identifier of the network port through which the LLDP frame was sent.
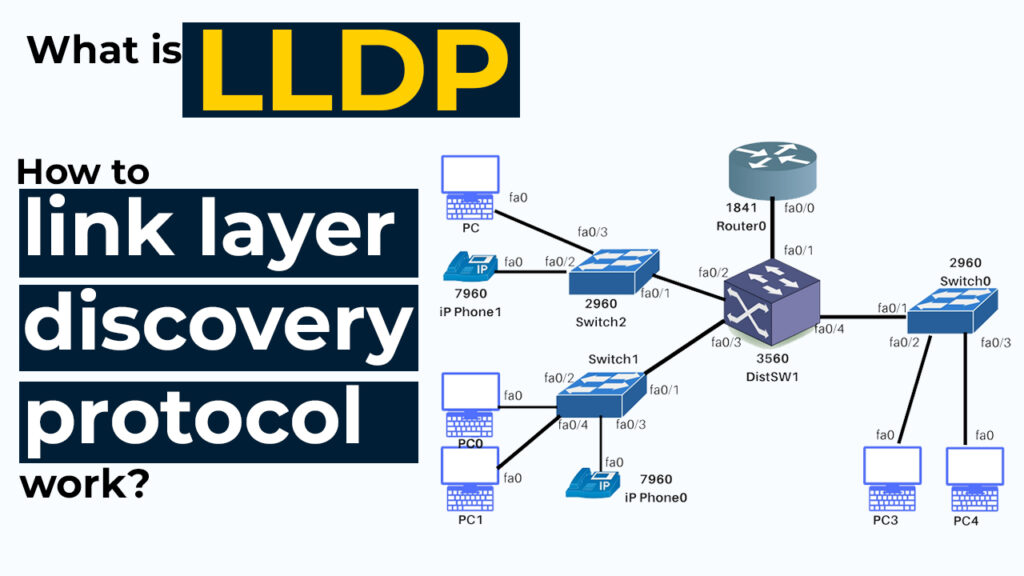
link layer discovery protocol Gain Practical Experience
- Lab Setup: Create a lab environment with networking equipment such as switches, routers, and computers. You can use physical devices or set up a virtual lab using software like GNS3 or Packet Tracer.
- Enable LLDP: Access the configuration interface of your networking devices (switches and routers) and enable LLDP. The exact steps may vary depending on the manufacturer and model of your equipment. Refer to the device’s documentation for guidance.
- LLDP Configuration: Configure link layer discovery protocol settings, such as the interval at which LLDP frames are sent and received, and specify which LLDP TLVs (Type, Length, Value) to include in the frames. You may also want to set up LLDP-MED (LLDP for Media Endpoint Devices) for more advanced capabilities.
- View link layer discovery protocol Information: Use the command-line interface or web interface of your networking devices to view LLDP information. Most devices have commands like “show LLDP neighbors” or “display LLDP neighbors” to display details about neighboring devices.
- Hands-On Labs: Look for online tutorials or hands-on labs related to LLDP. Many educational platforms and networking courses provide guided exercises for configuring and using link layer discovery protocol.
- Real-World Scenarios: Consider applying LLDP in real-world scenarios, such as in an enterprise network or a home network, to gain practical experience in a production environment.
- Certification Preparation: If you’re studying for network certifications like CCNA, CCNP, or CompTIA Network+, LLDP is a topic often covered in these exams. Slink layer discovery protocol in your labs to prepare for certification exams.
By following these steps and actively working with LLDP in a lab environment, link layer discovery protocol you can gain practical experience and develop valuable skills in network management and troubleshooting using the Link Layer Discovery Protocol.
HOW DO link layer discovery protocol Specialize.
- Wireless Networks: LLDP can be specialized for wireless networks, helping administrators identify access points, wireless clients, and optimize wireless network performance
- Network Security: Security professionals can leverage LLDP to enhance network security. For instance, LLDP can be used to detect rogue devices or unauthorized connections by comparing discovered device information with an approved device list.
- Voice over IP (VoIP) Networks: In VoIP environments, LLDP can be specialized to prioritize voice traffic and provide Quality of Service (QoS) settings. This ensures that voice calls have low latency and high quality.
- Network Management: LLDP is commonly used in network management to discover and map network topologies, monitor network links, and identify connected devices. Network administrators and IT professionals specialize in using LLDP as a tool to optimize network performance and troubleshoot issues.
- Voice over IP (VoIP) Networks: In VoIP environments, LLDP can be specialized to prioritize voice traffic and provide Quality of Service (QoS) settings. This ensures that voice calls have low latency and high quality.
Network Management: LLDP is commonly used in network management to discover and map network topologies, monitor network links, and identify connected devices. Network administrators and IT professionals specialize in using link layer discovery protocol as a tool to optimize network performance and troubleshoot issues.
Conclusion ink
As technology continues to evolve, LLDP remains a foundational protocol for maintaining, managing, and securing networks, making it an essential component of the ever-expanding world of networking and communications.